Specific Energy's Approach to Password Security
An application’s approach to password security is a foundational piece of building a strong authentication scheme. As part of Specific Energy’s efforts to maintain a strong security posture, the application has controls in place that go beyond those found in most authentication schemes. Common attacks the application is designed to mitigate include phishing, attacks that leverage data breaches to take advantage of password re-use across applications, and brute-force.
Resistance to phishing
Phishing attacks can be very dangerous and are frequently the source of compromised accounts. An example of a common phishing attack involves an attacker tricking a user into supplying credentials (say for the Specific Energy application) on an application hosted by the attacker rather than the legitimate application the user intended to visit. This could be in the form of an email that the attacker has crafted to appear that it came from the target application instructing the user to log in for some urgent reason via a link that takes the user to a clone of the application designed to harvest credentials. A well-designed attacker application clone might prompt for the user’s password a couple of times, telling them their first attempt failed (in case it actually did as they likely won’t know if they’ve harvested the correct password or if the user made a typo), and then re-direct them to the real application so the user can proceed without suspecting anything.
One safe-guard Specific Energy employs to mitigate this attack is requiring two-factor authentication on all user accounts. This comes in the form of users supplying a TOTP (time-based-one-time-password) during the authentication flow. A benefit of TOTP use during authentication is that it increases the difficulty for an attacker to successfully phish a user’s username, password, and TOTP code due to the fact that the TOTP code is only valid for 60 seconds. During account activation, a QR code containing a random seed is saved to a user’s mobile TOTP application (such as Google Authenticator) and is used to compute a 6-digit one-time-password that's valid for a 60 second window. Because TOTP is an offline calculation being done by your phone (with time and the random seed being the only inputs), it is resistant to SIM swapping attacks which target SMS based multi-factor authentication.
What can you do to make yourself more phishing resistant?
- Use a password manager and corresponding browser extension - Even the most diligent users cannot be trusted to ensure that the spelling of the domain they’ve visited is identical to the one they have an account for. Any decent password manager mitigates this issue by programmatically checking the domain matches the one for a stored password and that the connection to the site was negotiated over HTTPS (unless the user had explicitly stated otherwise when the password was saved). If your password manager doesn’t auto-fill your credentials STOP and think twice before continuing because you may be on a phishing website.
- Be wary of phishy messages - It is extremely difficult to avoid a well designed phishing attack but keep in mind that we will NEVER ask for your credentials over any medium that does not involve you personally inputting them into the application. You can always navigate the to the login page of our application via https://dashboard.specificenergy.com or you can find the link on the front page of https://specificenergy.com. Additionally you can navigate via the URL saved by your password manager
Limiting the Blast Radius of Data Breaches
Data breaches of one application can lead to breaches of accounts in another. For example, if a user with the email address “unsuspecting@victim.com“ has an account registered for Netflix and somehow (by exploiting a vulnerability in the application or through unauthorized access to backup systems) an attacker obtains a copy of Netflix’s user database, an attacker can proceed to attempt to recover passwords or “crack“ password hashes contained in the database. If the attacker were to crack the corresponding password hash for unsuspecting@victim.com in the Netflix database, the attacker could then test for password re-use across other applications that the victim could have accounts for (i.e. Amazon, Bank of America, etc.).
Even if Specific Energy users choose to reuse passwords across applications (you would never do that right? 😉), they are protected from a data breach of another application due to two-factor authentication being enabled on all accounts. This introduces entropy to the login process that cannot be shared across applications and stops an attacker from compromising a Specific Energy account if the user’s password is recovered as a result of a breach of another company’s user database.
Argon2id hashing
Offline brute-force attacks typically involve an attacker using a list of millions of common passwords to attempt to reproduce a hash in the database with a corresponding salt. The attacker would then compromise any accounts for which they were able to recover the password. A key characteristic of a strong password hashing algorithm is that it’s computationally expensive and difficult to parallelize so that offline attacks like these are more expensive for attackers to perform at any reasonable rate.
Although the Specific Energy application has many controls in place to prevent user data from falling into the wrong hands, to limit the impact of a data breach to the Specific Energy application, it uses a strong password hashing algorithm in the form of salted Argon2id hashes. The Argon2id variant of the Argon2 algorithm is a hybrid of Argon2d and Argon2i. The Argon2d algorithm optimizes for protection against GPU or ASIC accelerated attacks by accessing memory in a password dependent order but is susceptible to side-channel attacks if an attacker is able to locally observe the machine performing Argon2d hashes. The Argon2i variant is optimized for protecting against side-channel attacks by accessing memory in a password independent order. Argon2id, being a combination of both, delivers both resistance to hardware accelerated hash cracking and side-channel attacks.

What can you to do make yourself more resistant to data breaches?
- Use a password manager - Password managers allow you to generate unique, high-entropy passwords for each application and will notify you of any password re-use across applications.
- Sign up for data breach notifications - Troy Hunt (a renowned security researcher) developed Have I been Pwned which, among other things, allows you to sign up for free notifications of data breaches involving your email address. This allows you to stay on top of any services that are breached by changing any affected passwords.
Have u been pwned?
Another way that passwords can be more resistant to brute-force attacks is by users having high-entropy passwords. Many of us have seen the xkcd comic giving a classic example of how an application’s password strength rules (lower-case, upper-case, special character, etc.) often fail its users. However, Specific Energy takes the approach of checking proposed passwords (during password reset or account creation) against Have I been pwned’s extensive database of known weak or compromised passwords. This database of known compromised passwords is a result of aggregating password hashes obtained from data breaches over the years and currently consists of over 600 million passwords. Password lists generated from data breaches are often used by attackers to carry out brute-force attacks as they serve as a great representation of commonly used passwords. This makes checking proposed passwords against the HIBP database to be particularly valuable as it decreases the effectiveness of these attacks.
In addition to checking passwords against the HIBP database while setting a new password, existing passwords are checked for existence in the database on each successful login. If a user’s password was seen in a more recent data breach than when they originally established their password with the Specific Energy application, the user will be prompted to change their password during their next login as shown below.
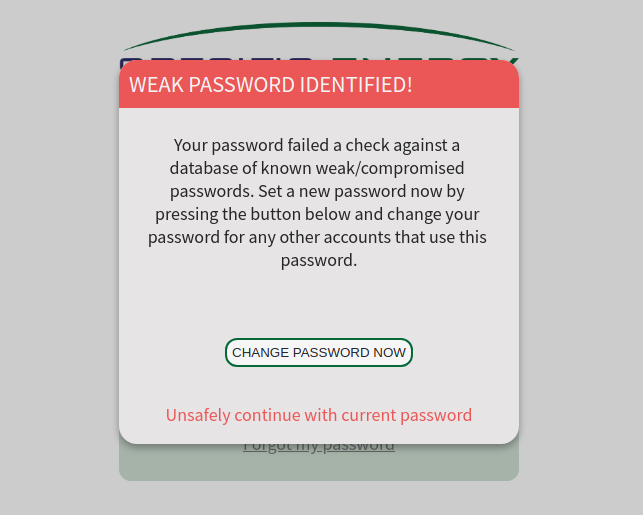
Some of you may be thinking “Isn’t it a bad idea to trust a third-party service, even one with good intentions, with something as sensitive as a user’s password?“. Have I Been Pwned has a clever solution that negates the need to trust their API for checking a password for existence in its database. The clear-text password is never sent to HIBP but rather only the first 5 hex characters of a SHA-1 hash of the password are supplied to the API. The API typically has many full SHA-1 hashes that have characters that match the supplied first 5 characters so they send back a long list of hashes with the remaining 35 hex characters. It is then up to the application that has the cleartext password (i.e. the Specific Energy application) to determine if the full SHA-1 hash was returned in the response from HIBP. You can read more about how HIBP uses what’s called k-anonymity to achieve this.
In summary
The Specific Energy application is designed to mitigate many common attacks against authentication schemes. Although the application makes no assumptions about the security preparedness of its users, we strongly encourage users to make use of a password manager to set high-entropy passwords and take advantage of automatic URL validation to resist phishing attacks.