Oldsmar Breach Highlights Cybersecurity Weaknesses
The complex technology, systems, applications, processes, and staffing that go into ensuring the public has a steady and safe supply of drinking water is not only threatened, but under attack. The vast number of cybersecurity threats to water utilities have been known, but more recently attacks exposed these cyber vulnerabilities to the public. On February 5, 2021 an unknown person gained unauthorized remote access to a water treatment plant in Oldsmar, Florida and increased the setpoint of sodium hydroxide fed into the drinking water system to a dangerous level. Although the breach was “immediately” noticed and the change in dosing was corrected before any meaningful impact to the drinking water occurred, this event highlighted several vulnerabilities many public water systems face in addressing cybersecurity threats.
The breach at Oldsmar occurred twice (5 hours apart), and it was only luck that an operator witnessed signs of the breach as the screen cursor moved and the setpoint was changed on the screen they were viewing at the time. It is reported that TeamViewer (a remote desktop application) was installed on the computers that the plant uses to review the status of controls and used by operators to monitor the plant controls remotely. Based on the reported state of the cybersecurity controls at the Oldsmar system, such a breach could have occurred at any time in the past. The Oldsmar attack was enabled by three key vulnerabilities that, if addressed, would have gone a long way in preventing the attack from occurring:
-
A common, simple, and unchanged password was used for all TeamViewer applications within the organization. The software was no longer used but left running on all systems.
-
The Oldsmar plant implemented a flat network with no firewall protecting computers from remote access.
-
The plant was also using an operating system that was beyond End of Life (EOL) and no longer supported with security patches from Microsoft.
In a word, such a breach was inevitable.
Water Utility Cybersecurity Threats and Vulnerabilities
Many public water utilities, like Oldsmar, are in a similar situation. COVID-19 accelerated the necessity for remote unmanned facilities. Limited funding forced many utilities to provide remote access for operations inside a network that has adopted very few cybersecurity controls. Utilities are threatened by cyber criminals of all kinds: script kiddies (unskilled cybercriminals with access to powerful programs), social engineers (cybercriminals intent on tricking the organization into installing remote access program or other breach), insiders (disgruntled employees or ex-employees with knowledge and access), and even state-sponsored terrorists looking to instill a sense of danger and panic. Many water utilities are unprepared and extremely vulnerable to these threats given the state of their network and cybersecurity program.
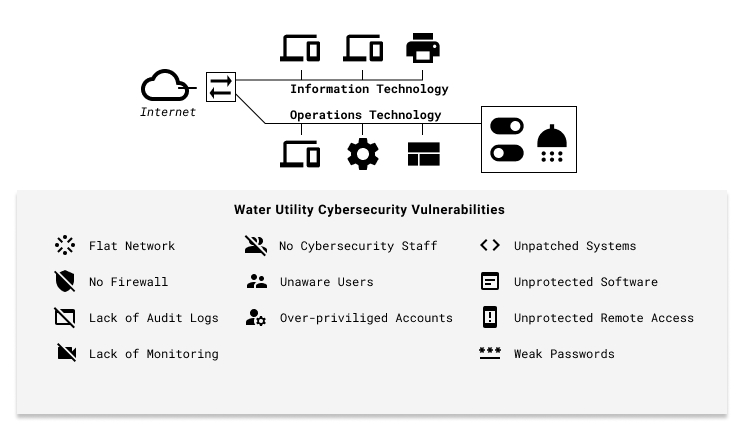
These cybersecurity threats are now aimed at the soft target of public water utilities. Government and industry studies have highlighted the many vulnerabilities exist within the Operational Technology (OT) and Information Technology (IT) systems at public water utilities. These include network issues (flat networks with limited border protections); staff issues (no cybersecurity staff, unaware users, and over-privileged accounts); system issues (unpatched systems, unauthorized software, unprotected remote access, and weak passwords); and oversight issues (no audit logs and no monitoring).
Top 14 Cybersecurity Recommendations for Water Utilities
The need for remote access for operations and remote control is not going away, but there are measures that can significantly decrease risk. Public water utilities may have limited funding and resources available to address all cybersecurity vulnerabilities. However, with an increased focus on cybersecurity hygiene and high-profile hacks, like the one at Oldsmar, these organizations can take big steps to effectively address these gaping holes. No list of cybersecurity recommendations will address all possible threats to an organization’s systems. However, a list is a great starting point for any organization looking to reduce their risk of cybersecurity incidents and accompanying losses. The following recommendations are aimed to providing the most efficient and effective improvements given the resource restrictions facing many utilities:
Basic Network and System Recommendations:
-
Install firewalls at all network entry points. Enable logging and implement the concept of “default deny all”.
-
Implement network segmentation (separate and isolate sensitive network resources through firewalls or software defined networks).
-
Patch all systems, applications, and browsers. Enable automatic security updates.
-
Establish unique accounts for each individual: no shared or group accounts or passwords allowed.
-
Implement strong authentication/password hygiene: require strong and unique passwords and two factor authentication.
-
Install anti-malware and spam protection software.
-
Provide security awareness training to protect against social engineering.
-
Collect and review logs: audit network usage, remote connection protocol / remote desktop usage, and unusual activity.
Advanced Security Control and Staffing Recommendations:
-
Inventory network and control system devices. Ensure all exposure to outside networks are known and addressed.
-
Employ cybersecurity staff; educate existing staff with professional cybersecurity training.
-
Implement a vendor security risk management program, vet 3rd parties with access.
-
Implement a mobile device management solution.
-
Include executives in cybersecurity awareness; quarterly reports; independent review.
-
Investigate all cybersecurity incidents.
Closing Thought
Any advice on addressing organizational cybersecurity gaps needs to be tempered with a recognition that performing these reviews internally is challenged by the inexperience, bias, and conflict of interest among the organization’s current resources. To overcome these obstacles the organization should seek to:
-
Obtain an independent cybersecurity assessment – An independent cybersecurity consultant does this for a living and is able to quickly and objectively identify the best path for creating a strong cybersecurity program.
-
Outsource cybersecurity services wherever possible – Keeping up with the latest threats, attacks, and patches is a full-time endeavor. Outsource whenever you can to companies that excel at providing a secure service. There are automation vendors like Specific Energy that work to stay on top of threats and vulnerabilities to allow users to focus on the important job of maintaining a clean, safe supply of drinking water.

Douglas Landoll, CEO, Lantego — Douglas Landoll has over three decades of information security experience. He has led over 100 cybersecurity risk assessments, established security programs for top corporations and government agencies, and trained over 3000 cybersecurity professionals. He is an expert in security risk assessment, security risk management, security criteria, and building corporate security programs and the author of three cybersecurity books. www.lantego.com.